Welcome
Data is at the core of all that we do — regardless of whether for your business, our clients, or in our home life. We have to see what to look like after secret data with the goal that it doesn’t fall into the off-base hands, either purposely or inadvertently. We are on the whole in charge of data security, which isn’t just about IT related themes, yet how we utilize advanced data and physical records everyday.
Information Security covers:
- Physical security i.e. the offices we work in. It includes things like alarm systems, barriers, window and door locks etc.
- Personnel security i.e. who we employ and how we look after them. It includes things like vetting and training
- Data security i.e. how we protect the data and information we look after for our customers as well as our own needs. This includes paper documents as well as electronic files
- Technology security i.e. the systems we use to protect the data. So this is about the IT, and includes things like antivirus software
We have a lawful prerequisite to ensure individual data consistently under the Data Protection Act, and there are numerous other order of information which are liable to stringent information insurance necessities because of industry guideline, for example, monetary information, government limited information and charge/MasterCard information. Our customers likewise endow us to process and store their information safely inside the arrangements and administrations we give. Data Security is a piece of all that we do in our jobs, and taking care of business is a key part of Web Tech Solutions (Peter Rusu) accomplishment.
In this module, you will see approaches to keep your own data secure.
You will:
- Comprehend the significance of gathering and discarding individual data safely
- Reveal approaches to defend your information in open spots
- Identify suspicious behavior and the ways in which criminals may gain access to your personal data
- Perceive moves that you can make to shield the information of your customers and clients
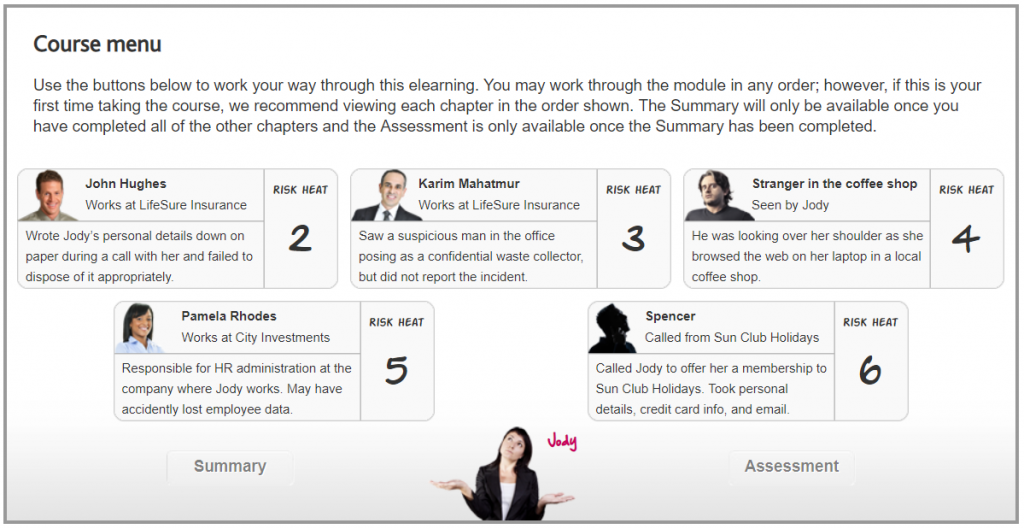
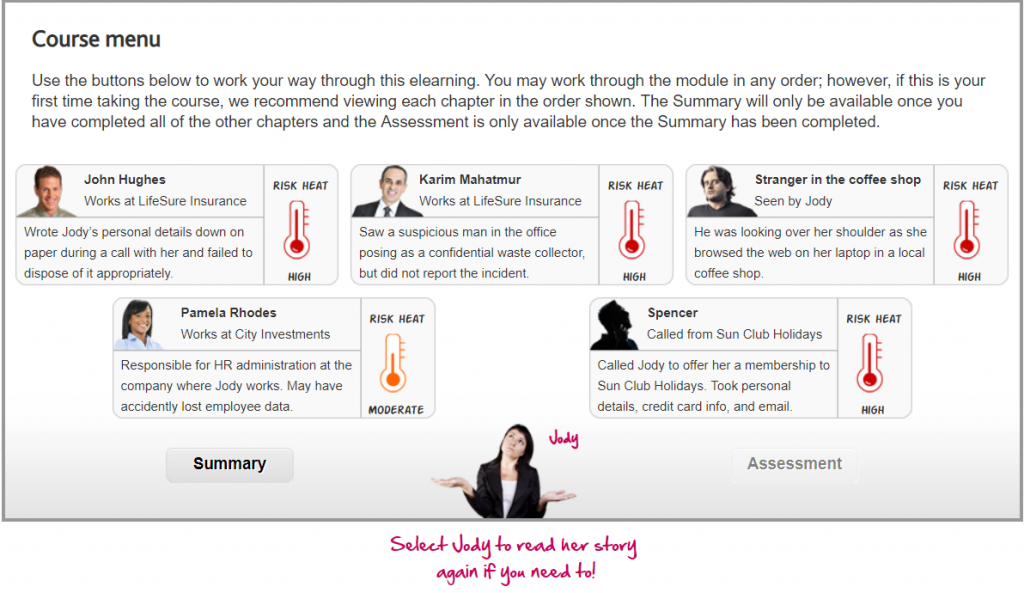
Meet Jody …
This is Jody . She works in the money related administrations industry in the City of London, so is very much aware of the ascent in monetary wrongdoing over ongoing years. Be that as it may, a year ago Jody got herself the casualty of a genuine instance of focused personality and monetary misrepresentation. All through this module, we’ll research how Jody was focused by fraudsters and what she, and others, could have done to anticipate it.
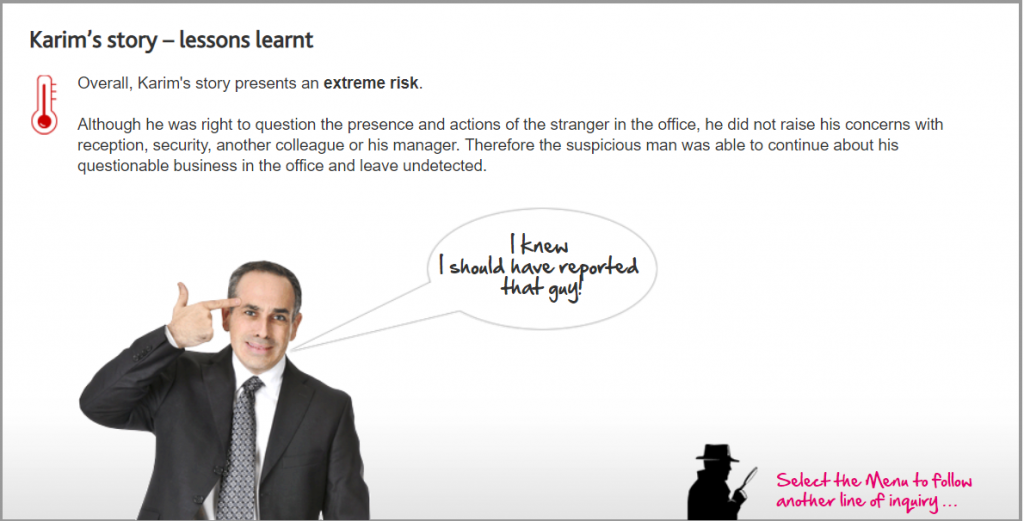
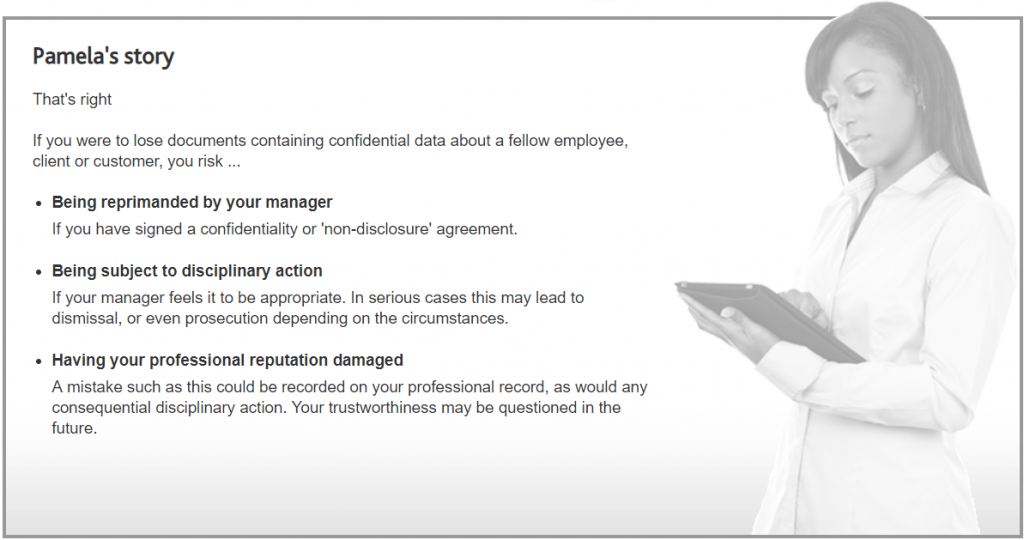
That’s correct
Karim was entirely justified in thinking that the man seemed suspicious; after all, he works in the office five days a week and is likely to notice if something unusual occurs.
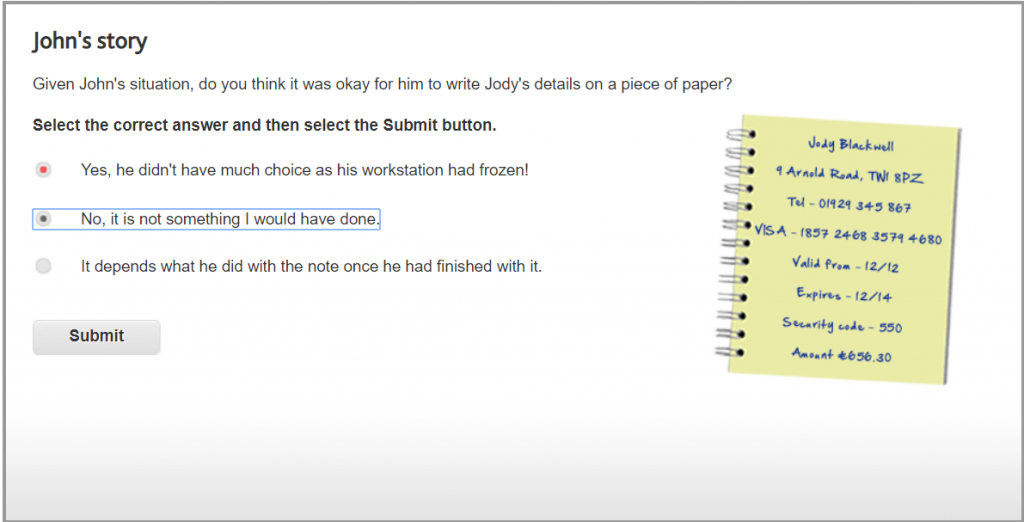
If the files and folders are no longer required, the safest option is to place them in the confidential waste for secure shredding or shredded with a cross cut shredder.
This is the only safe way of disposing of ‘Confidential’ information if you have no means of passing it back to the person who printed it. You must always dispose of ‘Confidential’ material safely.

DVDs may contain personal details or business ‘Confidential’ information. They should always be disposed of securely.

Web-Tech.Solutions Password Security requirements are user account passwords must be at least 8 case-sensitive characters in length.

Non-dictionary word combinations of letters, numbers and special characters are the most difficult for fraudsters to guess.
If you make a contribution, first check that the site you are visiting is secure. As a general rule, never forward chain emails – the list of email addresses quickly grows to hundreds if not thousands, and each email address can then be compromised by hackers and fraudsters.
If you forward emails such as this, delete existing email addresses from the original email and blind copy (BCC) your recipients so that the address list does not build up.

Never open suspicious emails or attachments from unknown sources, as viewing either the message or opening the attachment can be harmful.
This is the most appropriate response and ensures that our business reputation is maintained.

The safest option is to ask a relative to arrange and purchase the flowers from their more secure location, and pay them back after the journey is completed.

If you have your laptop with you as you travel by car, always ensure you place your laptop in the boot of the car from the start of the journey.
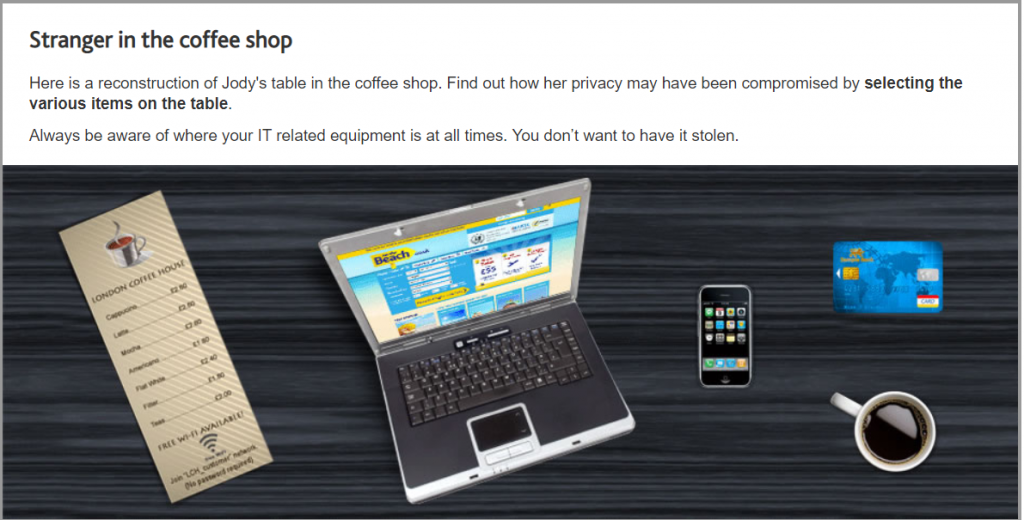
Laptops that are left exposed, for example on back seats are a temptation to thieves. They can just as easily see you move the laptop into the boot, and have been known to target people doing just that.

Always keep laptops and briefcases containing company information with you and never let them out of your sight.

You must never take photographs or videos onsite without permission. If there is a business requirement to take photographs around the office, first obtain permission from your local Information Security Manager or your Divisional InfoSec Resources.
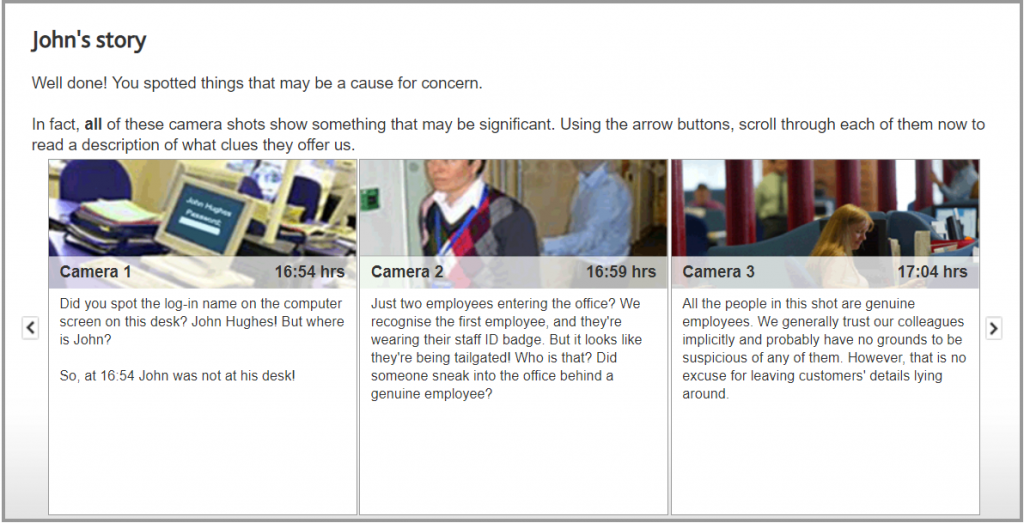
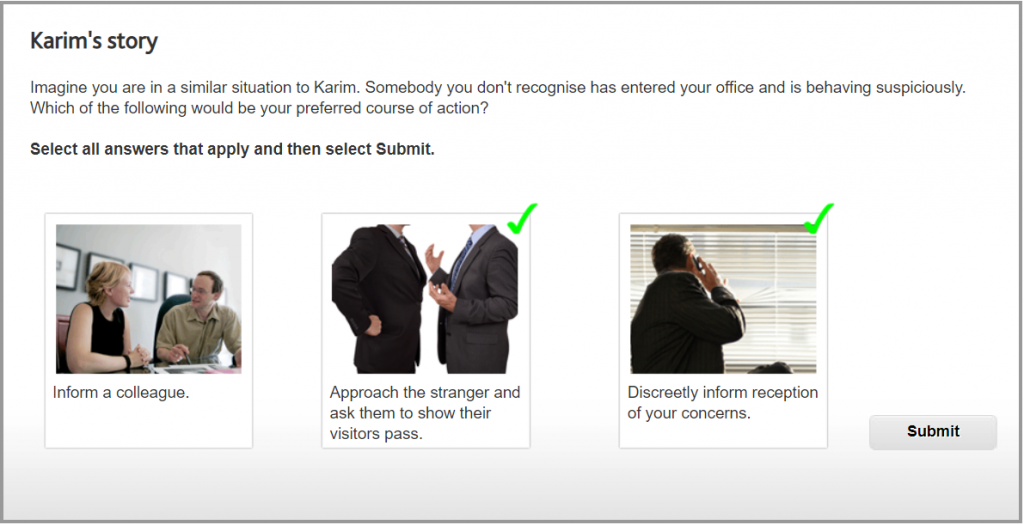
We all have a responsibility to ensure the people in the office have a legitimate reason for being there. Introducing yourself and having a conversation might be a friendly thing to do, but ask to see someone’s ID badge if it is not displayed and/or if you do not recognise them, rather than leaving it up to your colleagues.
You must challenge those not wearing appropriate identification. Your local security guard or reception must also be notified if you are suspicious about a person’s presence in the office, so they can contact the police if necessary, as well as instigate any other standard procedures following a breach of security.
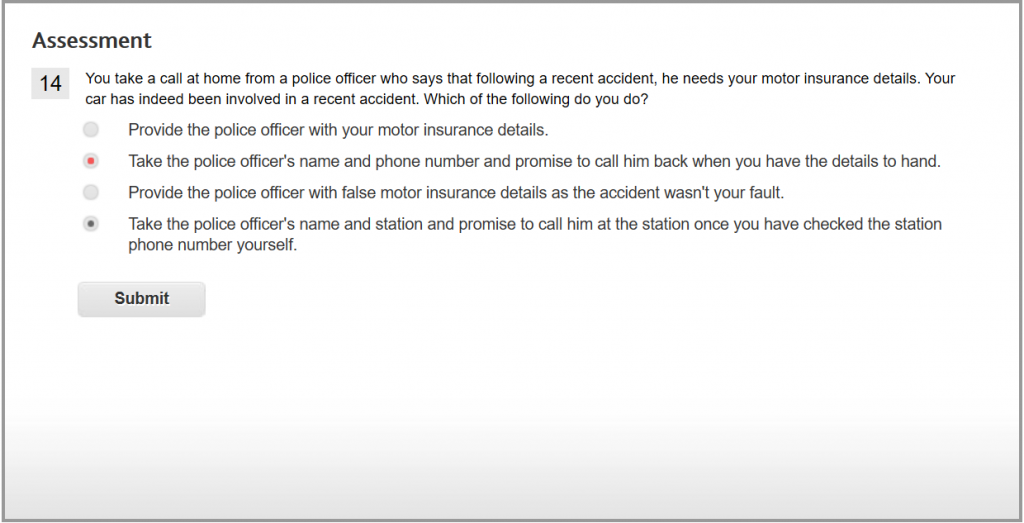
This is the safest option. If the caller really is a police officer, the police station will know of him and put you through.

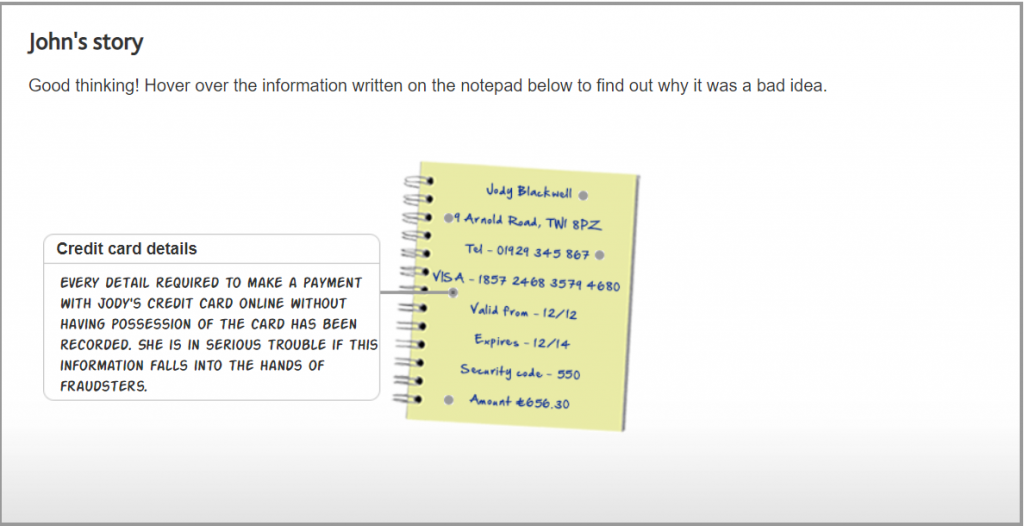
Any document that contains personal information such as name, address, date of birth, National Insurance number, next of kin, a photograph, and your signature could easily put you at risk if it fell into unscrupulous hands.
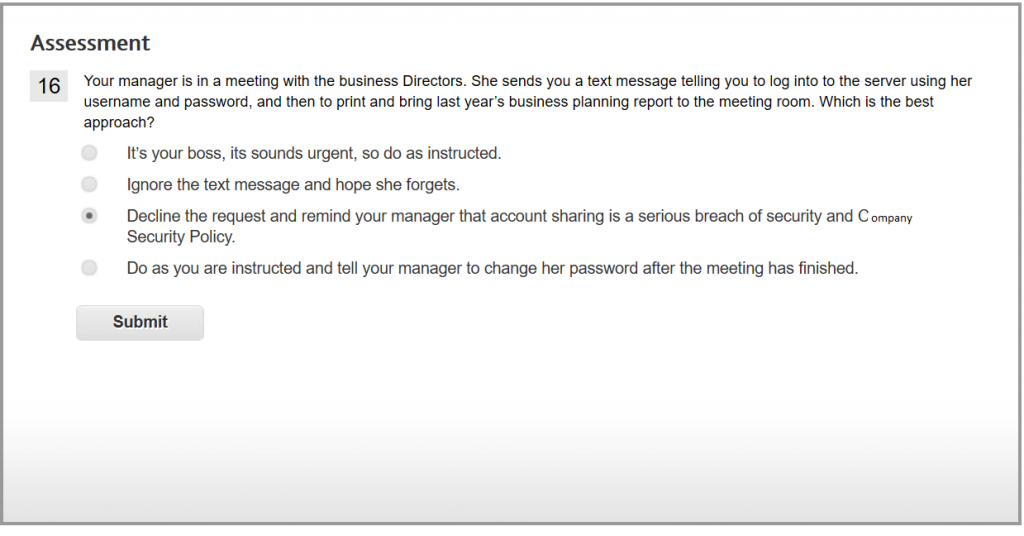
Correct. Sharing a user ID and password with another member staff, even when instructed by someone in a more senior role, is a serious breach of Web-Tech Solutions’s Security Policy and may result in disciplinary action. If the text message contained the manager’s username and password, or the manager had previously shared her account credentials, then it must be reported as a security incident.
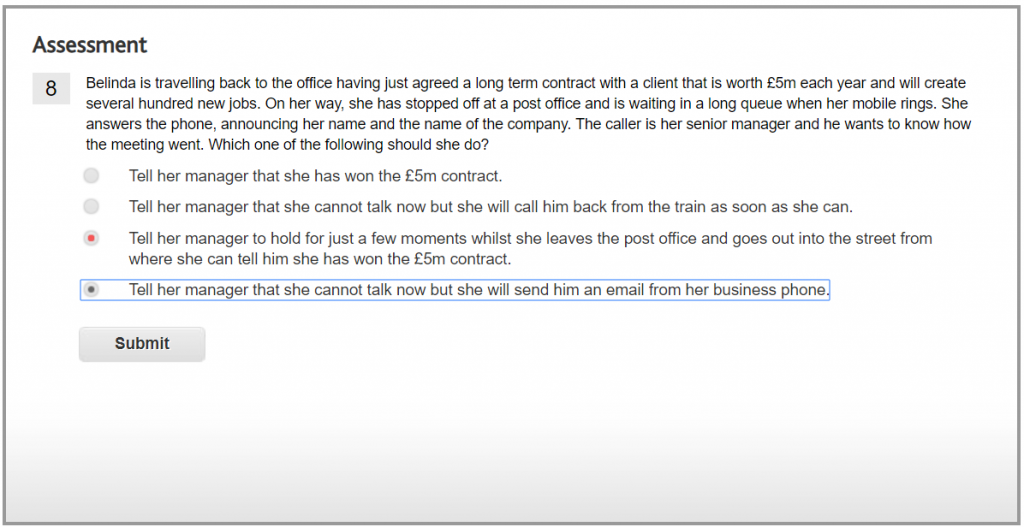
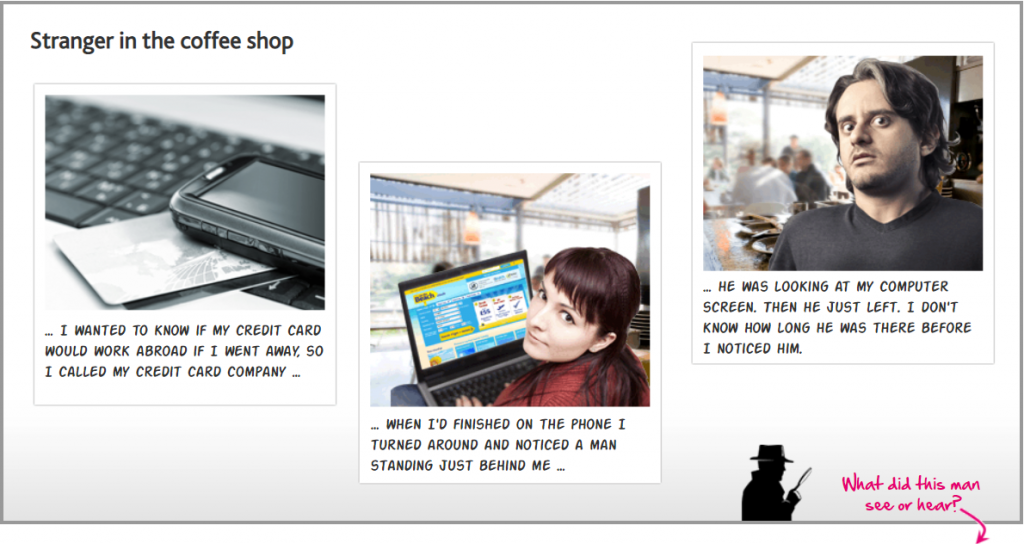
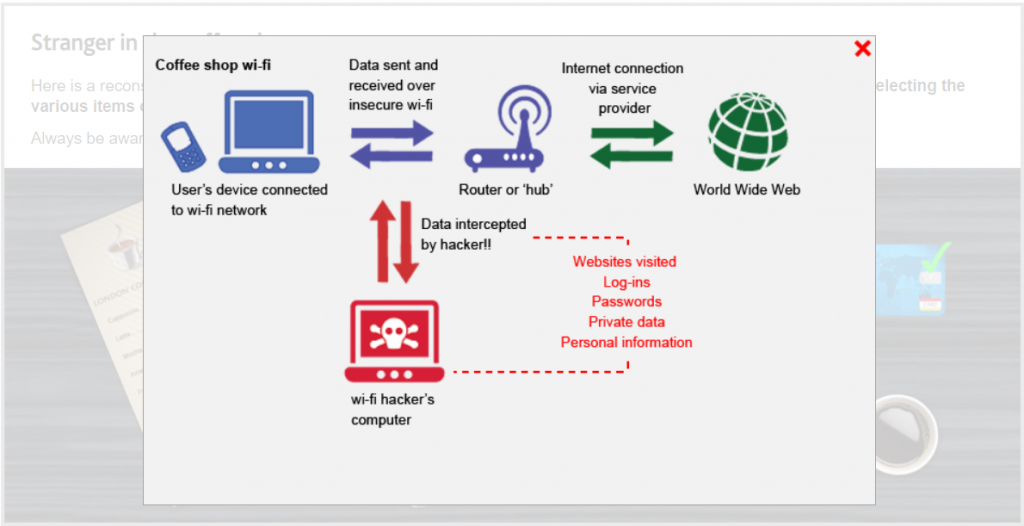
This is the safest option and one which her line manager should respect. You must always be wary of eavesdroppers in public places.
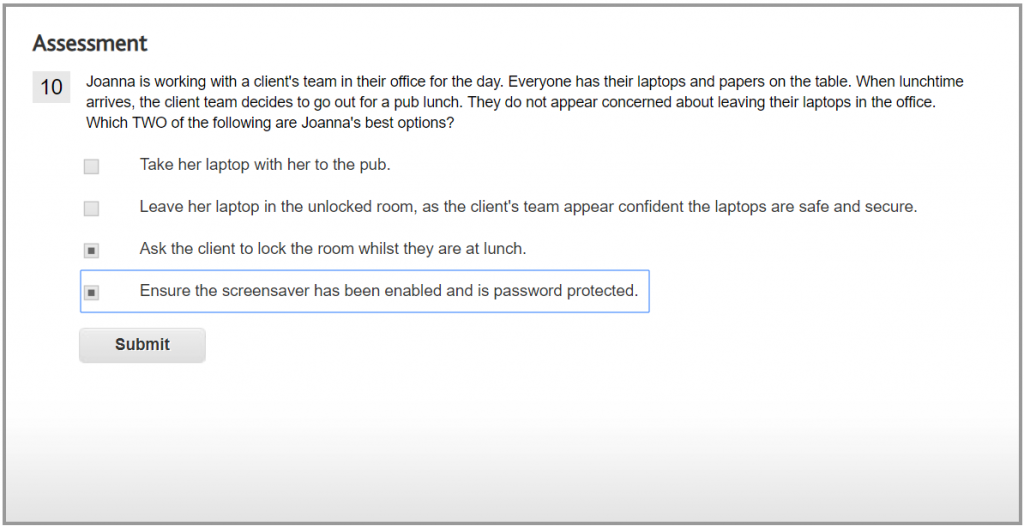
Always ask clients to lock rooms which contain laptops and/or other business papers and password enable the screensaver. This ensures that laptop contents are protected if others return to the room first.
This action is the one which will most significantly reduce risk. The BlackBerry supplier can be contacted immediately and access to the phone can be barred preventing loss of ‘Confidential’ information on Anna’s phone.
You are responsible for keeping equipment safe and secure; never leave ‘Confidential’ or sensitive documents unattended.
Always lock your computer screen using a password protected screensaver when you leave your desk, no matter for how short a period, and ensure you have locked away any sensitive or ‘Confidential’ files and papers in a drawer or other secure place.
If you have nowhere to lock your files and papers, or you are not in a company office, take them with you to your meeting.

You should be suspicious of anyone who does not know their date of birth or mother’s maiden name (if their mother’s maiden name is held on file)!

Always obtain permission from the source of the request before sharing information about the company, or any other personal or ‘Confidential’ information.